Cybersecurity researchers have discovered an Android banking malware campaign that has leveraged a trojan named Anatsa to target users in North America using malicious apps published on Google’s official app marketplace.
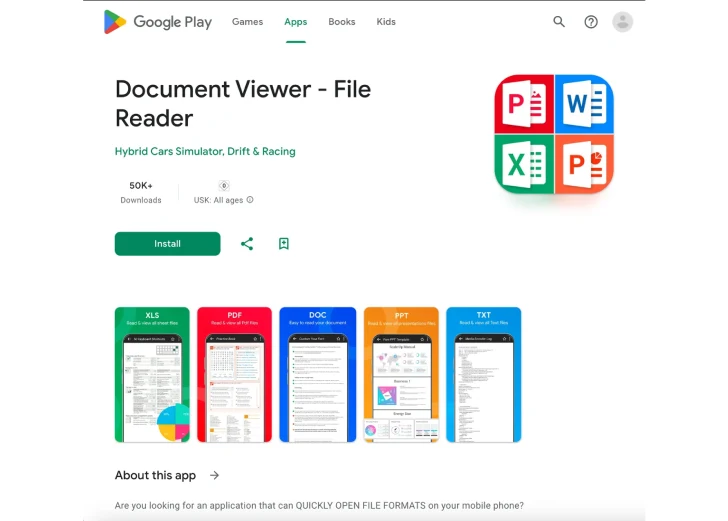
The malware, disguised as a “PDF Update” to a document viewer app, has been caught serving a deceptive overlay when users attempt to access their banking application, claiming the service has been temporarily suspended as part of scheduled maintenance.
“This marks at least the third instance of Anatsa focusing its operations on mobile banking customers in the United States and Canada,” Dutch mobile security company ThreatFabric said in a report shared with The Hacker News. “As with previous campaigns, Anatsa is being distributed via the official Google Play Store.”
Anatsa, also referred to as TeaBot and Toddler, has been known to be active since at least 2020, typically delivered to victims via dropper apps.
Early last year, Anatsa was found to have targeted Android device users in Slovakia, Slovenia, and Czechia by first uploading benign apps masquerading as PDF readers and phone cleaners to the Play Store and then introducing malicious code a week after release.
Like other Android banking trojans, Anatsa is capable of providing its operators with features designed to steal credentials through overlay and keylogging attacks, and conduct Device-Takeover Fraud (DTO) to initiate fraudulent transactions from victim’s devices.
ThreatFabric said Anatsa campaigns follow a predictable, but well-oiled, process that involves establishing a developer profile on the app store and then publishing a legitimate app that works as advertised.
“Once the application gains a substantial user base – often in the thousands or tens of thousands of downloads – an update is deployed, embedding malicious code into the app,” the company said. “This embedded code downloads and installs Anatsa on the device as a separate application.”
The malware then receives a dynamic list of targeted financial and banking institutions from an external server, enabling the attackers to perform credential theft for account takeover, keylogging, or fully automated transactions using DTO.
A crucial factor that allows Anatsa to evade detection as well as maintain a high success rate is its cyclical nature where the attacks are interspersed by periods of no activity.
The newly discovered app targeting North American audiences masquerades as a Document Viewer (APK package name: “com.stellarastra.maintainer.astracontrol_managerreadercleaner”) and is published by a developer named “Hybrid Cars Simulator, Drift & Racing.” Both the app and the associated developer account are no longer accessible on the Play Store.
Statistics from Sensor Tower show that the app was first published on May 7, 2025, reaching the fourth spot in the “Top Free – Tools” category on June 29, 2025. It’s estimated to have been downloaded around 90,000 times.
“This dropper followed Anatsa’s established modus operandi: initially launched as a legitimate app, it was transformed into a malicious one approximately six weeks after release,” ThreatFabric said. “The distribution window for this campaign was short yet impactful, running from 24 to 30 June.”
The Anatsa variant, per the company, is also configured to target a broader set of banking apps in the United States, reflective of the malware’s increasing focus on exploiting financial entities in the region.
Another clever feature incorporated into the malware is its ability to display a fake maintenance notice when trying to access the target banking application. This tactic not only conceals the malicious activity occurring within the app, but also prevents customers from contacting the bank’s support team, thereby delaying detection of financial fraud.
“The latest operation not only broadened its reach but also relied on well-established tactics aimed at financial institutions in the region,” ThreatFabric said. “Organizations in the financial sector are encouraged to review the provided intelligence and assess any potential risks or impacts on their customers and systems.”