Just in the first six months of 2025, the crypto industry has lost over US$2.1 billion across at least 75 separate incidents, due to hacks and exploits. What’s startling to note is that the amount is nearly equal to the total losses recorded for 2024, according to data from TRM Lab’s latest report.

Far from being the usual crimes of opportunity, the recent scale and sophistication of the attacks reveal how crypto is becoming a battleground for geopolitical cyber conflict.
State-sponsored actors are now testing their skills against critical financial infrastructure, pushing the boundaries of international finance and exploiting the borderless, currently mid-to-unregulated nature of the crypto ecosystem.
TRM Labs’ analysis highlights the key risks shaping crypto’s threat landscape in 2025.
The Bybit Breach Proved That Cold Wallets Aren’t Impenetrable
Nothing illustrates the severity of crypto hacks more clearly than the catastrophic Bybit incident back in February this year. The attack accounted for over US$1.5 billion in total losses via Ethereum tokens, surpassing all previous exploits on record.
TRM Labs’ confirmed that North Korean hackers were responsible for the breach using blockchain intelligence, identifying links between the wallets used in this incident and those tied to previous North Korean thefts. The FBI confirmed the link of the heist to North Korea on 26 February 2025.
The attribution fits a well-established pattern of cyberattacks linked to Pyongyang, which TRM Labs estimates has stolen more than US$5 billion in crypto since 2017. The Bybit breach follows North Korea’s playbook almost exactly, which targets centralised crypto exchanges through phishing, supply chain attacks, and the theft of private keys.
These same tactics were seen in the 2023 Atomic Wallet hack, where over US$100 million of cryptocurrency was drained from more than 4,100 wallets. Adding on, TRM’s North Korea expert and former FBI subject matter expert, Nick Carlsen, shared,

“The Bybit exploit indicates that the regime is intensifying its “flood the zone” technique—overwhelming compliance teams, blockchain analysts, and law enforcement agencies with rapid, high-frequency transactions across multiple platforms, thereby complicating tracking efforts.”
Beyond the sheer scale of the Bybit hack, the speed at which the stolen funds were laundered is equally alarming.
Within just 48 hours, about US$160 million had already been funnelled through illicit channels. By 23 February 2025, TRM Labs estimated the total had surpassed US$200 million, and just three days later, more than US$400 million had been moved.
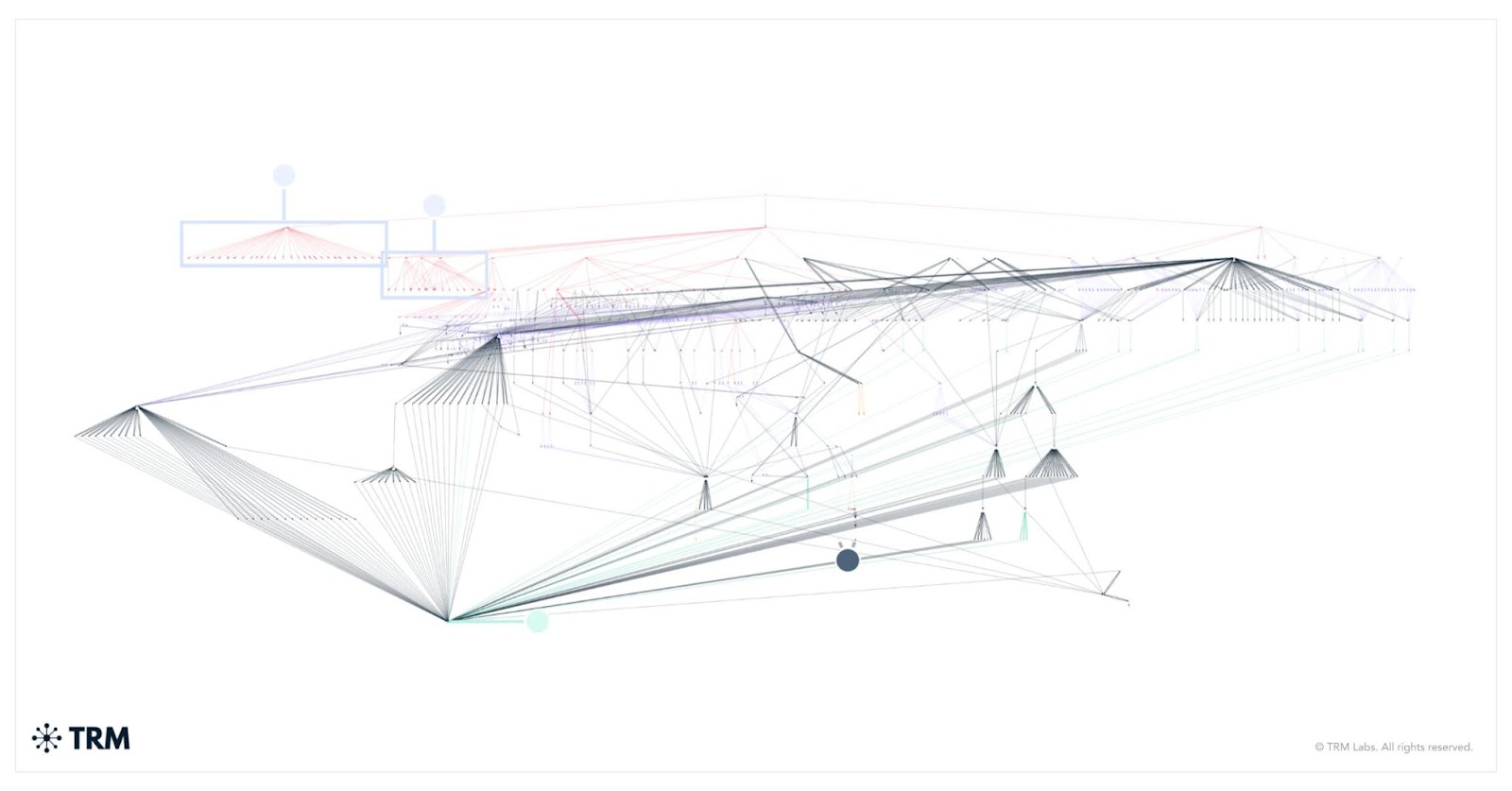
The operation’s sheer scale, velocity and clear operational efficiency are pushing traditional anti-money laundering frameworks to their limits, making it increasingly difficult for investigators to keep pace.
A Geopolitical Dimension to Crypto Crime
Beyond the Bybit hack, analysis by TRM Labs on crypto hacks for the first half of 2025 also brought to light emerging threats from other state-aligned groups. While North Korea still remains a dominant actor, another notable case involved a group reportedly linked to Israel, known as Gonjeshke Darande or Predatory Sparrow.
This group was tied to the breach of Nobitex on 18 June 2025, said to be Iran’s biggest crypto exchange, for US$90 million. Gonjeshke Darande claimed responsibility for the attack, stating it targeted the platform for its alleged role in helping the Iranian regime evade international sanctions and fund illicit operations.
Yet, in a striking twist, the attackers funnelled the stolen funds to vanity addresses that were deemed “unspendable”. By sending funds to wallets with no known private keys, the funds were permanently inaccessible.
This suggests that the group never had the intention or perhaps the capability to access the funds, pointing to a motive that was likely symbolic or political rather than financial.
It’s a stark reminder that digital asset theft is quickly becoming a tool in state-driven agendas and geopolitical conflicts.
Rethinking Crypto Defence and the Dire Need for Collaboration
As state-backed attacks grow bolder and losses hit record highs, players in the crypto industry will need to harden their defences, and soon. The best foot forward would require collaboration from several fronts.
Tackling state-backed crypto crime demands tighter collaboration between global law enforcement, financial intelligence units, and blockchain analytics firms. Preemptive information sharing and coordinated cross-border efforts will be essential for tracking and recovering stolen assets while sending a clear message of deterrence.
The coming months will be a critical test of whether the crypto ecosystem can evolve quickly enough before the next mega-hack occurs.
Featured image by Who is Danny on Freepik